Firefox Enable DNS over HTTPS and NoScript???
Firefox Enable DNS over HTTPS and NoScript???
Today I got a pop-up message in Firefox about "Enable DNS over HTTPS" (FAQ). When enabling/disabling this feature you can choose a provider (Cloudflare is Default). If I don't have Cloudflare "Trusted" in NoScript will this cause issues with this feature, or is this feature "behind the scenes" and NoScript is not involved?
Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Re: Firefox Enable DNS over HTTPS and NoScript???
Although I'm not using this setting in my Firefox*, I'm fairly certain that cloudflare doesn't have to be set to Trusted in NoScript, as you're dealing with cloudflare for DNS resolution, not cloudflare as it might be employed for any particular website.
However, although from a security standpoint it is most likely secure enough, I do try to avoid cloudflare for DNS resolution, as they have a reputation for allegedly serving criminal, very shady or extremist sites. Plus they are still - albeit with excuses - providing service to Russia.
For that, do a search for
"Does cloudflare serve criminal or extremist websites?" and see what comes up.
However, you can avoid cloudflare entirely, the default for DOH in Firefox, and instead use Quad9, much to be preferred.
https://www.quad9.net/
Quite easy to set Quad9 for DNS resolution in Firefox. Just select Custom for User Provider and enter
https://dns.quad9.net/dns-query
In order to see what servers are actually being employed by your Quad9, just go to dnsleaktest.com

*Note, although the custom setting in Firefox is quite straightforward and easy to set up, in case you might be interested, I'm not using any of this directly in Firefox, using instead dnscrypt-proxy (for Mac) - exclusively with Quad9 resolvers. Sorry, no experience setting this up for Windows.
For more on that and to see directions to set this up for Windows and other OSs see:
https://github.com/DNSCrypt/dnscrypt-proxy
However, although from a security standpoint it is most likely secure enough, I do try to avoid cloudflare for DNS resolution, as they have a reputation for allegedly serving criminal, very shady or extremist sites. Plus they are still - albeit with excuses - providing service to Russia.
For that, do a search for
"Does cloudflare serve criminal or extremist websites?" and see what comes up.
However, you can avoid cloudflare entirely, the default for DOH in Firefox, and instead use Quad9, much to be preferred.
https://www.quad9.net/
Quite easy to set Quad9 for DNS resolution in Firefox. Just select Custom for User Provider and enter
https://dns.quad9.net/dns-query
In order to see what servers are actually being employed by your Quad9, just go to dnsleaktest.com

*Note, although the custom setting in Firefox is quite straightforward and easy to set up, in case you might be interested, I'm not using any of this directly in Firefox, using instead dnscrypt-proxy (for Mac) - exclusively with Quad9 resolvers. Sorry, no experience setting this up for Windows.
For more on that and to see directions to set this up for Windows and other OSs see:
https://github.com/DNSCrypt/dnscrypt-proxy
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Re: Firefox Enable DNS over HTTPS and NoScript???
Testing confirms this. Makes sense, since AFAIK WebExtensions can't intercept DNS resolution.
What makes you think any of that stuff has anything to do with their DNS service?
Last I checked, Quad9 does not "just do" DNS, they also filter malware domains - viewtopic.php?f=19&t=23567
When suggesting a DNS provider that does any sort of filtering, please make a point of mentioning that and the specific type(s) of filtering, because the reasons explained in viewtopic.php?p=80785#p80785 (even though Quad9's filtering is less likely to be problematic than the case that post was written for)
*Always* check the changelogs BEFORE updating that important software!
-
Re: Firefox Enable DNS over HTTPS and NoScript???
Thank you for the replys, I'll take a look at other providers.
Does anyone know if this DNS over HTTPS could affect your modem? I just found out about Firefox implementing this feature the other day. The pop-up appeared on the screen at the same time it notified me that version 99.0 was available. Before updating to 99.0 and clicking on the pop-up's Okay|Disable buttons, I went into the settings and the feature was already enabled.
So I don't know how long it's been enabled, but I've been having DNS issues since 2/24/22 where my modem would crap-out and my IP would change randomly. In the logs "dnsmasq[4655]: no responses from nameserver 'xx.xx.xx.xx'" show up before the IP change.
I think I'll disable the DNS over HTTPS via Firefox for a week and see if my modem still acts up.
Does anyone know if this DNS over HTTPS could affect your modem? I just found out about Firefox implementing this feature the other day. The pop-up appeared on the screen at the same time it notified me that version 99.0 was available. Before updating to 99.0 and clicking on the pop-up's Okay|Disable buttons, I went into the settings and the feature was already enabled.
So I don't know how long it's been enabled, but I've been having DNS issues since 2/24/22 where my modem would crap-out and my IP would change randomly. In the logs "dnsmasq[4655]: no responses from nameserver 'xx.xx.xx.xx'" show up before the IP change.
I think I'll disable the DNS over HTTPS via Firefox for a week and see if my modem still acts up.
Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Re: Firefox Enable DNS over HTTPS and NoScript???
That is completely unrelated as dnsmasq does not have DoH support. If this problem is DNS server related, you would need to change the system-wide DNS provider on that system - and enabling DoH in FIrefox should help, not make it worse. But I would suspect this is not DNS related at all, it seems more likely either a loose connection from modem to ISP or a larger issue with your modem.
*Always* check the changelogs BEFORE updating that important software!
-
Re: Firefox Enable DNS over HTTPS and NoScript???
kukla wrote: ↑
Fri Apr 08, 2022 10:01 am
I do try to avoid cloudflare for DNS resolution, as they have a reputation for allegedly serving criminal, very shady or extremist sites. Plus they are still - albeit with excuses - providing service to Russia.
Point taken, their reputation has nothing to do with DNS resolution. However, even though cloudflare is ubiquitous, almost impossible to avoid (like Amazon AWS - not a big fan of Amazon either) if possible I try to avoid direct use of anything cloudflare, just because their overall reputation doesn't pass the smell test. In fact, I'm running a third party firmware on my Asus router and, although I've given it my best effort, I have to use cloudflare DNS, at least there, for several mobile devices. No way there to do an end run around cloudflare and instead use DNSCrypt-proxy with Quad9 resolvers, which I am able to use on the desktops.barbaz wrote: What makes you think any of that stuff has anything to do with their DNS service?
As far as not offering that Quad9 is principally involved in malware filtering - not a small omission, I agree - xaex, the OP, would have seen that had xaex visited the Quad9 link I supplied.
As for the several links you posted about Quad9 possibly being problematic - don't want to belabor this by going though everything there - but the negatives in those replies either seem rather out of date (e.g., Quad9 now located in Sweden, not U.S.) a few of them rather far fetched, or just don't seem to apply. Not seeing any strong reasons not to use Quad9, in fact I think the filtering is a big plus.
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Re: Firefox Enable DNS over HTTPS and NoScript???
Maybe getting off-topic here (I'll split this if it becomes needed), but why are you forced to use Cloudflare? Maybe you can't use dnscrypt-proxy but surely you can configure the DNS service to use, no?
I would say, if the third-party firmware doesn't let you choose your DNS provider, maybe that's not a good third-party firmware to use.
Sorry I wasn't clear. I did not intend to suggest that Quad9 might be problematic, neither here nor in the other thread. I too am not seeing any strong reasons not to use Quad9, provided you're aware of its filtering.
The purpose of linking that thread was only that that was "last I checked" and is the discussion thread about Quad9 on this forum.
Quad9's current privacy policy looks better than the one they had at the time those posts were written.
*Always* check the changelogs BEFORE updating that important software!
-
Re: Firefox Enable DNS over HTTPS and NoScript???
The third party firmware is a branch of Tomato, "Fresh Tomato." (Have been using different versions of Tomato for years). Set this one up a few years ago, and was deep in the weeds with it then, but have forgotten so much by now. Probably overstated being "forced" to use Cloudflare - pretty certain there must be other options for DNS. Will have to open it up and see why, all things being equal, I felt that I had to settle on Cloudflare, which, if I recall, was the native option.
Will get back to you on this.
Will get back to you on this.
Last edited by kukla on Sun Apr 10, 2022 1:11 am, edited 1 time in total.
Mozilla/5.0 (iPad; CPU OS 9_3_5 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Version/9.0 Mobile/13G36 Safari/601.1
Re: Firefox Enable DNS over HTTPS and NoScript???
Feel free to split this off, maybe to Web Tech or Security?
Well have gone at least partially back into the weeds:
First off, big surprise, not using Cloudflare for DNS, using Quad9. (Resolvers listed are both Quad9). Not sure why I thought that was the case. Most likely because I have two different Asus routers running Fresh Tomato. Might have been confusing the current one with the one not in use, which could have been set to Cloudflare DNS as a compromise: dnscrypt-proxy used to be an option in earlier versions of Tomato, but no longer available, and also, for various reasons, no longer wanted to use OpenDNS, which I used use for any number of years. Have screenshots, but only way to tell for sure is to put the other Asus back in service and see - not quite ready for that.
Not sure how much further into the weeds you want to go, but current version of FT is FreshTomato Version 2020.2. Screenshot of part of Basic->Network page:
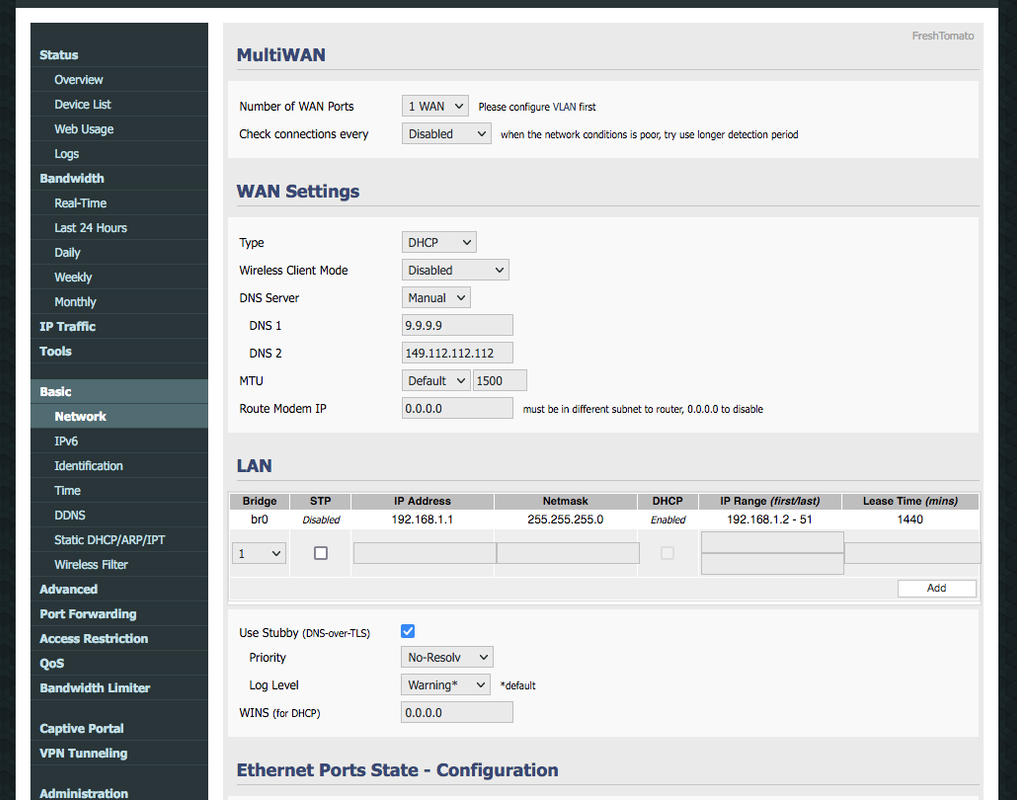
Some curious results running FT with and without Stubby enabled (DNS over TLS): with DNSCrypt-Proxy on the Macs, dnsleaktest shows all resolvers at woody.net (in NY), which is completely kosher and expected for Quad9 resolvers, but running dnsleaktest on an iPad Pro (a much later one, my wife's, running the current v.1.5.4.1, not my ancient one running iOS 9.3.5) with Stubby enabled 2 woody.net resolvers show - expected - along with 3 in the Netherlands. Not sure if this is a leak or not. But with Stubby disabled, I'm getting all the woody.net resolvers that I see on the Macs and none of the ones in the Netherlands. Big question mark around Stubby.
Ran several tests (tenta.com/test/ and https://www.cloudflare.com/ssl/encrypted-sni/#results) to check if DNS is encrypted, at least TLS, with and without Stubby enabled. Tests are inconclusive, both on the Macs, which I'm 100% certain has to be using encrypted DNS, and on the newer up to date iPad. Even with Stubby TLS enabled, the tenta one shows as TLS false on the Macs. (Both tests for Mac and iPad do show DNSSEC enabled). So not sure what to make of all this. Perhaps you know of other tests for DNS encryption which might be more solid or reliable?
EDIT: Also ran this one https://dnscheck.tools/#basic, both on Macs and iPad, with this result: "Great! Your dns responses are authenticated, protecting you from certain attacks!" Whatever dns responses authenticated is supposed to mean.
Well have gone at least partially back into the weeds:
First off, big surprise, not using Cloudflare for DNS, using Quad9. (Resolvers listed are both Quad9). Not sure why I thought that was the case. Most likely because I have two different Asus routers running Fresh Tomato. Might have been confusing the current one with the one not in use, which could have been set to Cloudflare DNS as a compromise: dnscrypt-proxy used to be an option in earlier versions of Tomato, but no longer available, and also, for various reasons, no longer wanted to use OpenDNS, which I used use for any number of years. Have screenshots, but only way to tell for sure is to put the other Asus back in service and see - not quite ready for that.
Not sure how much further into the weeds you want to go, but current version of FT is FreshTomato Version 2020.2. Screenshot of part of Basic->Network page:

Some curious results running FT with and without Stubby enabled (DNS over TLS): with DNSCrypt-Proxy on the Macs, dnsleaktest shows all resolvers at woody.net (in NY), which is completely kosher and expected for Quad9 resolvers, but running dnsleaktest on an iPad Pro (a much later one, my wife's, running the current v.1.5.4.1, not my ancient one running iOS 9.3.5) with Stubby enabled 2 woody.net resolvers show - expected - along with 3 in the Netherlands. Not sure if this is a leak or not. But with Stubby disabled, I'm getting all the woody.net resolvers that I see on the Macs and none of the ones in the Netherlands. Big question mark around Stubby.
Ran several tests (tenta.com/test/ and https://www.cloudflare.com/ssl/encrypted-sni/#results) to check if DNS is encrypted, at least TLS, with and without Stubby enabled. Tests are inconclusive, both on the Macs, which I'm 100% certain has to be using encrypted DNS, and on the newer up to date iPad. Even with Stubby TLS enabled, the tenta one shows as TLS false on the Macs. (Both tests for Mac and iPad do show DNSSEC enabled). So not sure what to make of all this. Perhaps you know of other tests for DNS encryption which might be more solid or reliable?
EDIT: Also ran this one https://dnscheck.tools/#basic, both on Macs and iPad, with this result: "Great! Your dns responses are authenticated, protecting you from certain attacks!" Whatever dns responses authenticated is supposed to mean.
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Re: Firefox Enable DNS over HTTPS and NoScript???
Quad9's website has a page showing their locations, can you use that to check?kukla wrote: ↑Sun Apr 10, 2022 4:56 pm running dnsleaktest on an iPad Pro (a much later one, my wife's, running the current v.1.5.4.1, not my ancient one running iOS 9.3.5) with Stubby enabled 2 woody.net resolvers show - expected - along with 3 in the Netherlands. Not sure if this is a leak or not.
Sorry, I don't. I wasn't aware there were completely external DNS tests like the ones you mention (i.e. neither local nor provided by the DNS provider in use). To test for encryption I would have just used something like Wireshark or tcpdump.
*Always* check the changelogs BEFORE updating that important software!
-